/docs subpath using AWS Route 53 and CloudFront, you need to configure your DNS provider to point to your CloudFront distribution.
High-level overview
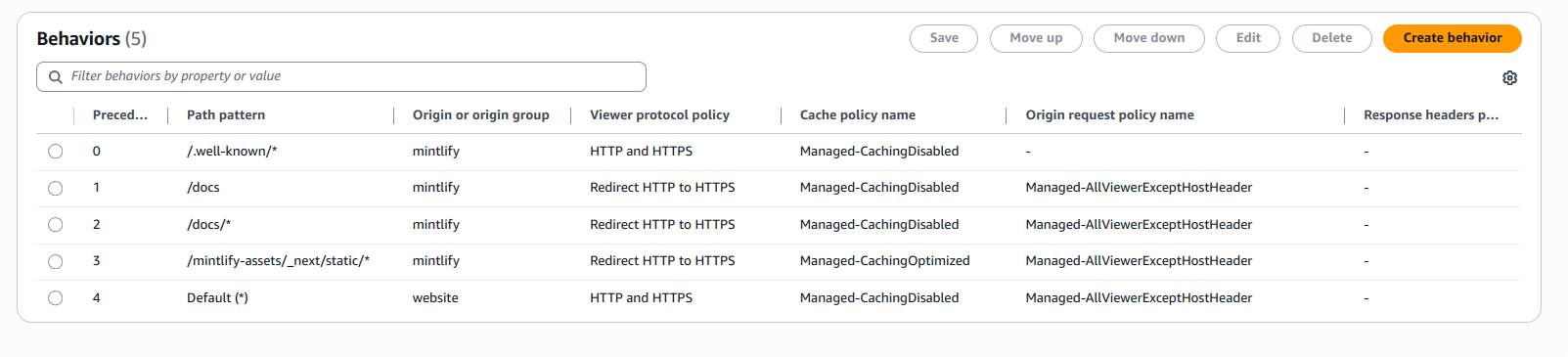
Route traffic to these paths with a Cache Policy of CachingDisabled:/.well-known/acme-challenge/*- Required for Let’s Encrypt certificate verification/.well-known/vercel/*- Required for domain verification/docs/*- Required for subpath routing/docs/- Required for subpath routing
/mintlify-assets/_next/static/*Default (*)- Your websites landing page
AllViewerExceptHostHeader.
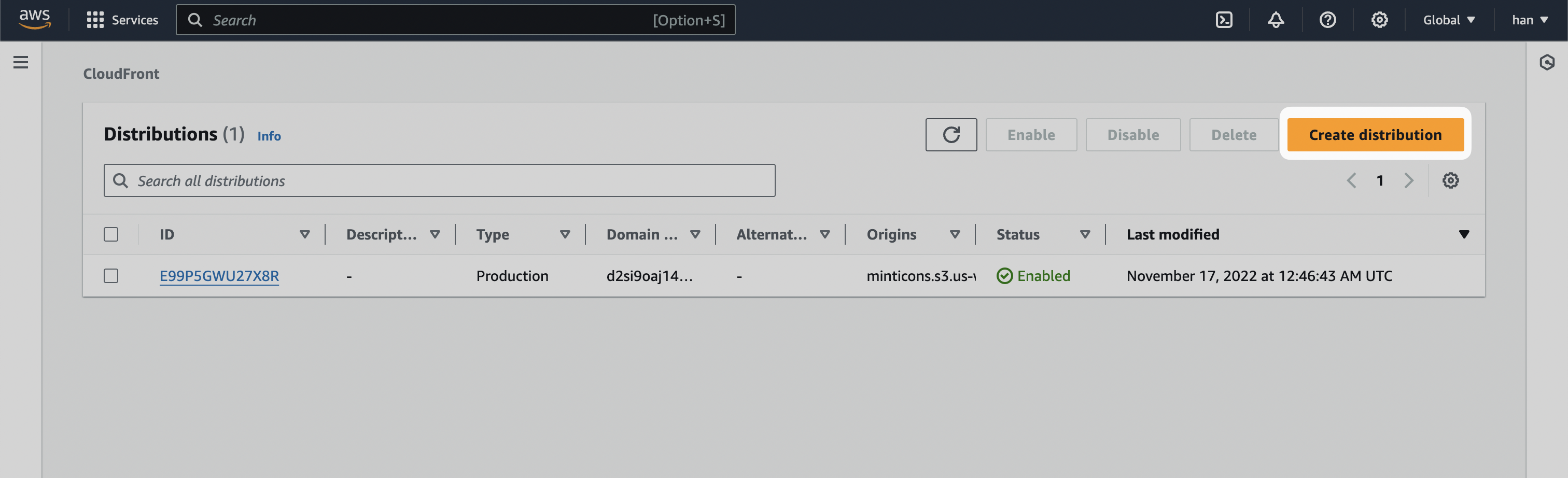
Create CloudFront distribution
- Navigate to CloudFront inside the AWS console.
- Select Create distribution.
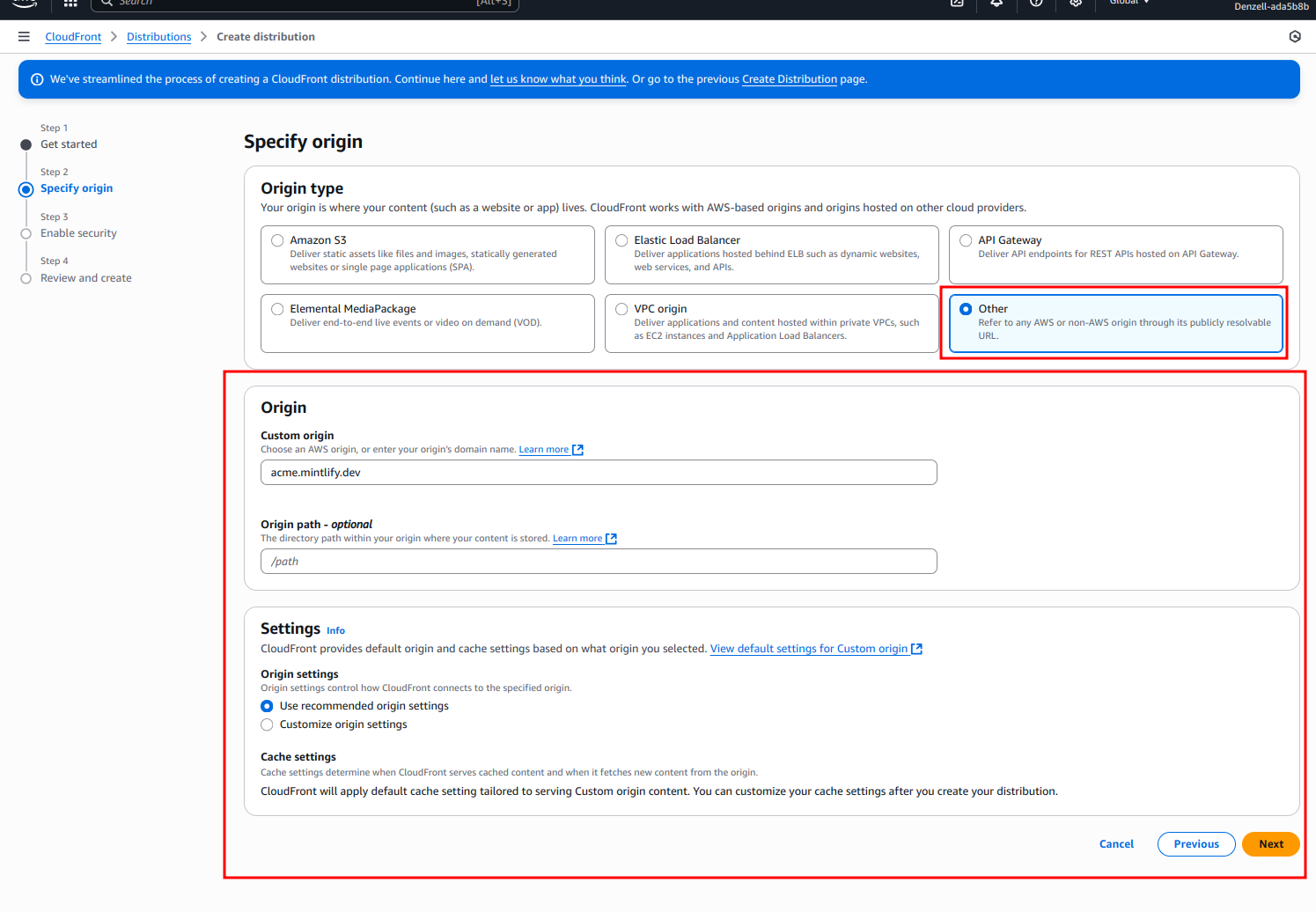
- For the Origin domain, input
[SUBDOMAIN].mintlify.devwhere[SUBDOMAIN]is your project’s unique subdomain.
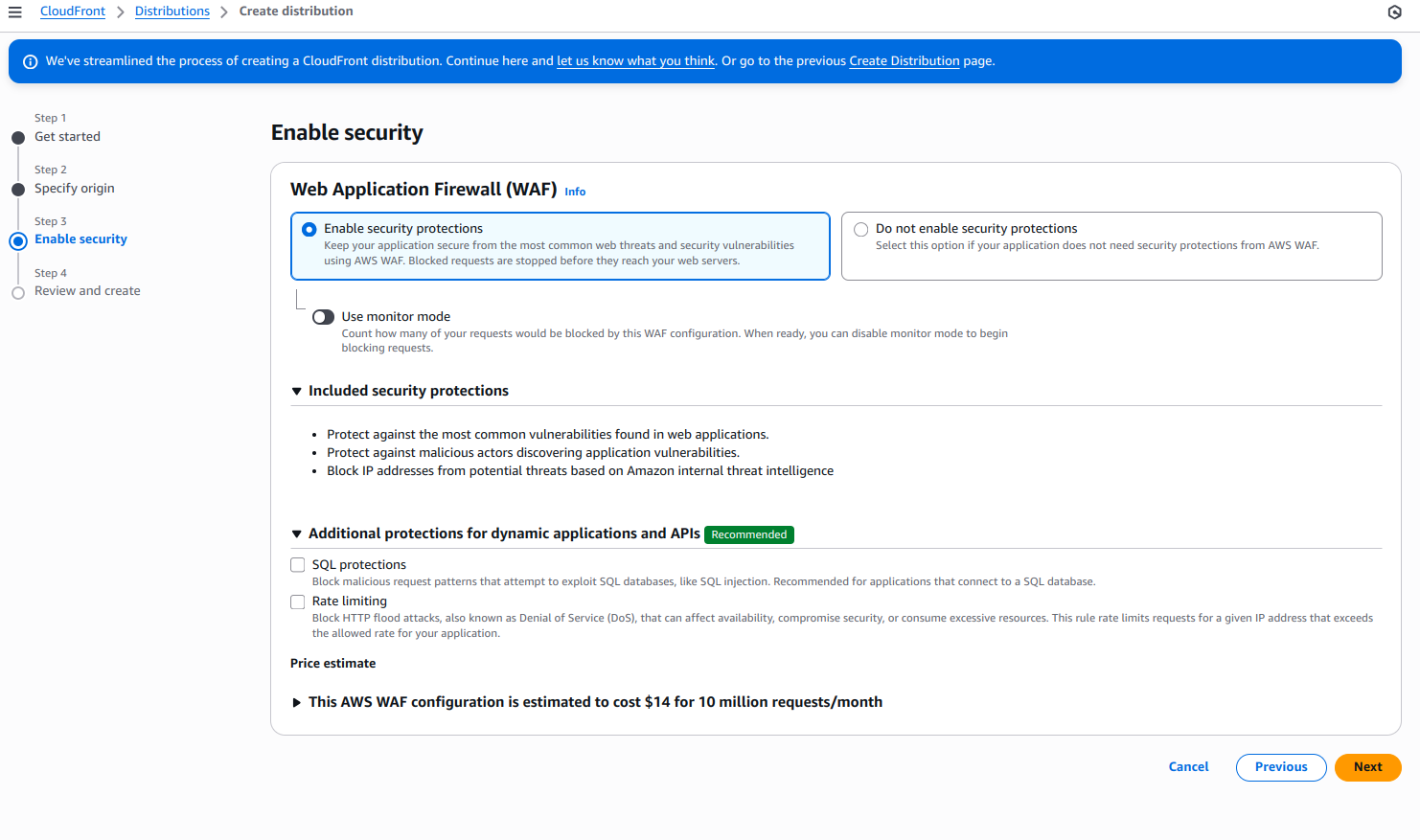
- For “Web Application Firewall (WAF),” enable security protections.
- The remaining settings should be default.
- Select Create distribution.
Add default origin
- After creating the distribution, navigate to the “Origins” tab.
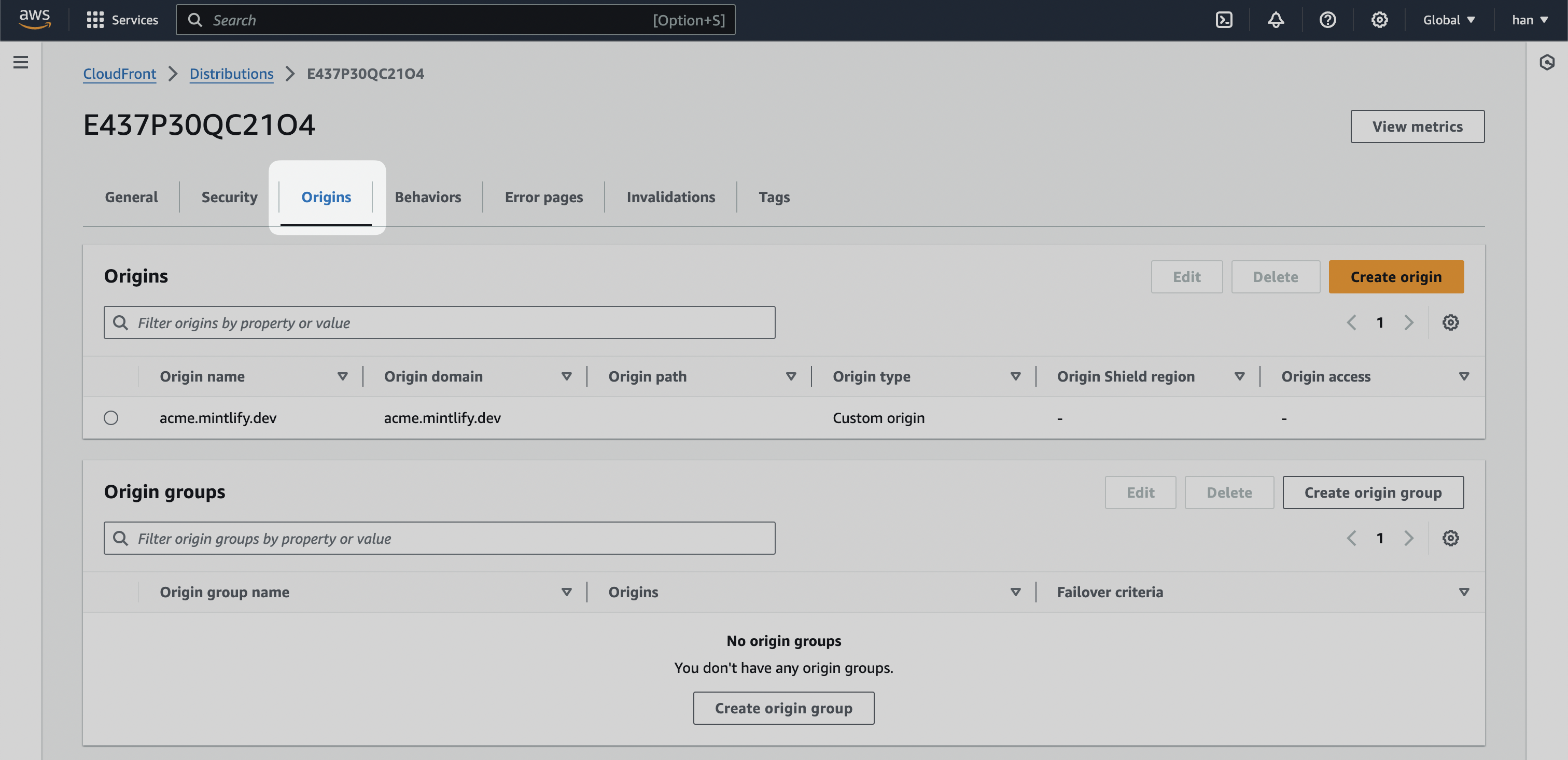
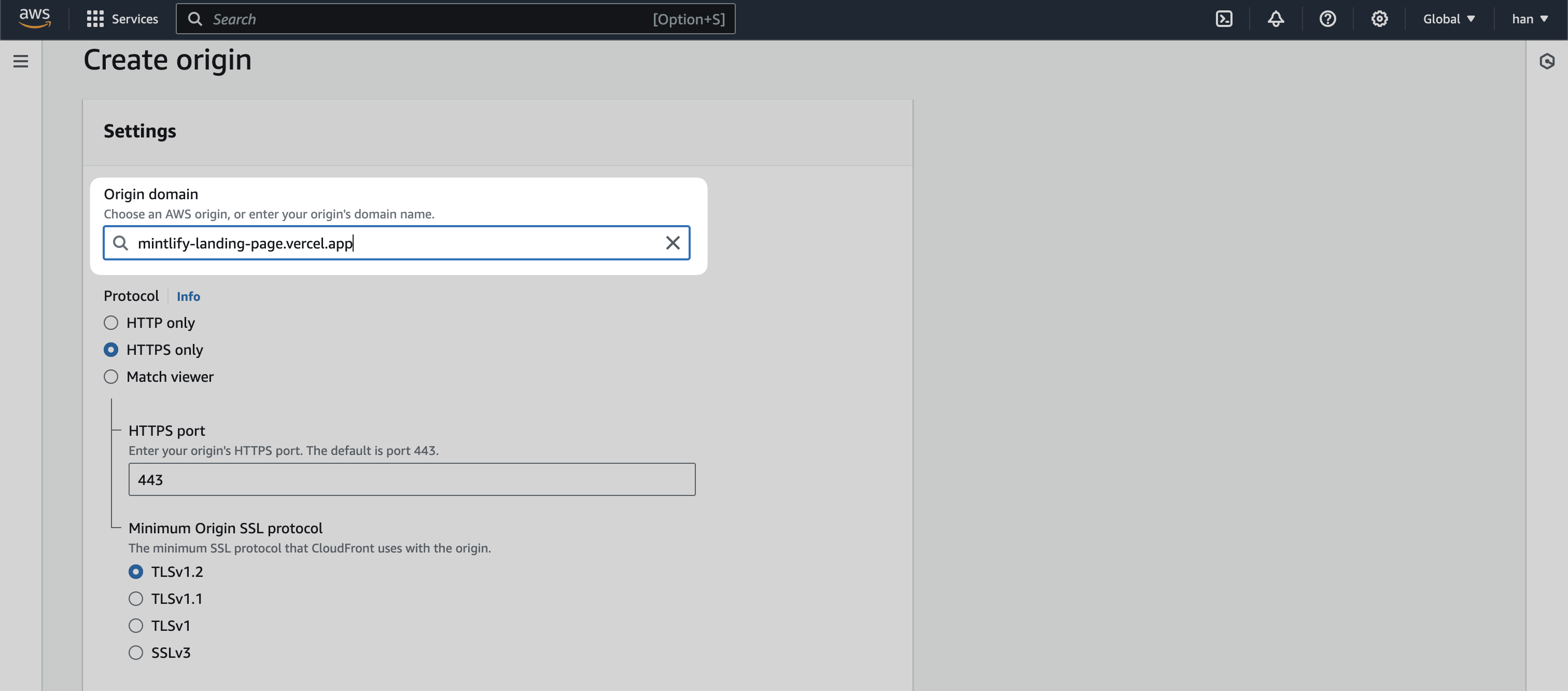
- Find your staging URL that mirrors the main domain. This is highly variant depending on how your landing page is hosted. For example, the Mintlify staging URL is mintlify-landing-page.vercel.app.
If your landing page is hosted on Webflow, use Webflow’s staging URL. It would look like
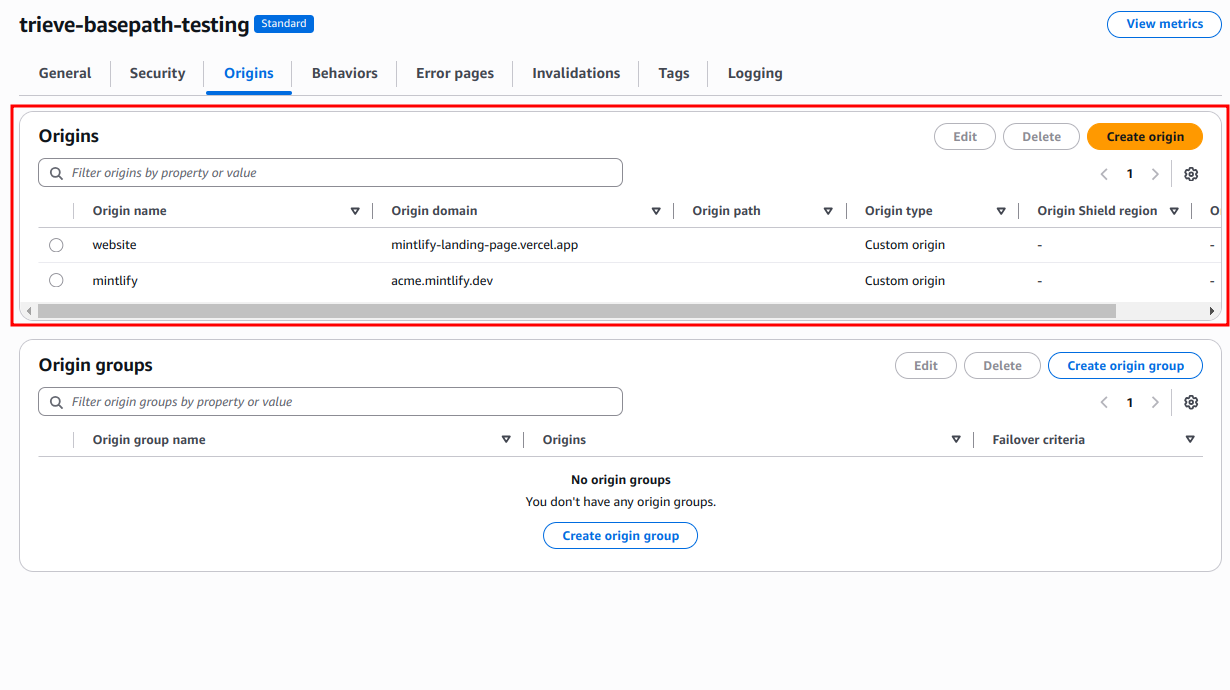
.webflow.io.If you use Vercel, use the .vercel.app domain available for every project.- Create a new Origin and add your staging URL as the “Origin domain”.
[SUBDOMAIN].mintlify.app and another with your staging URL.
Set behaviors
Behaviors in CloudFront enable control over the subpath logic. At a high level, we’re looking to create the following logic.- If a user lands on /docs, go to
[SUBDOMAIN].mintlify.dev. - If a user lands on any other page, go the current landing page.
- Navigate to the “Behaviors” tab of your CloudFront distribution.
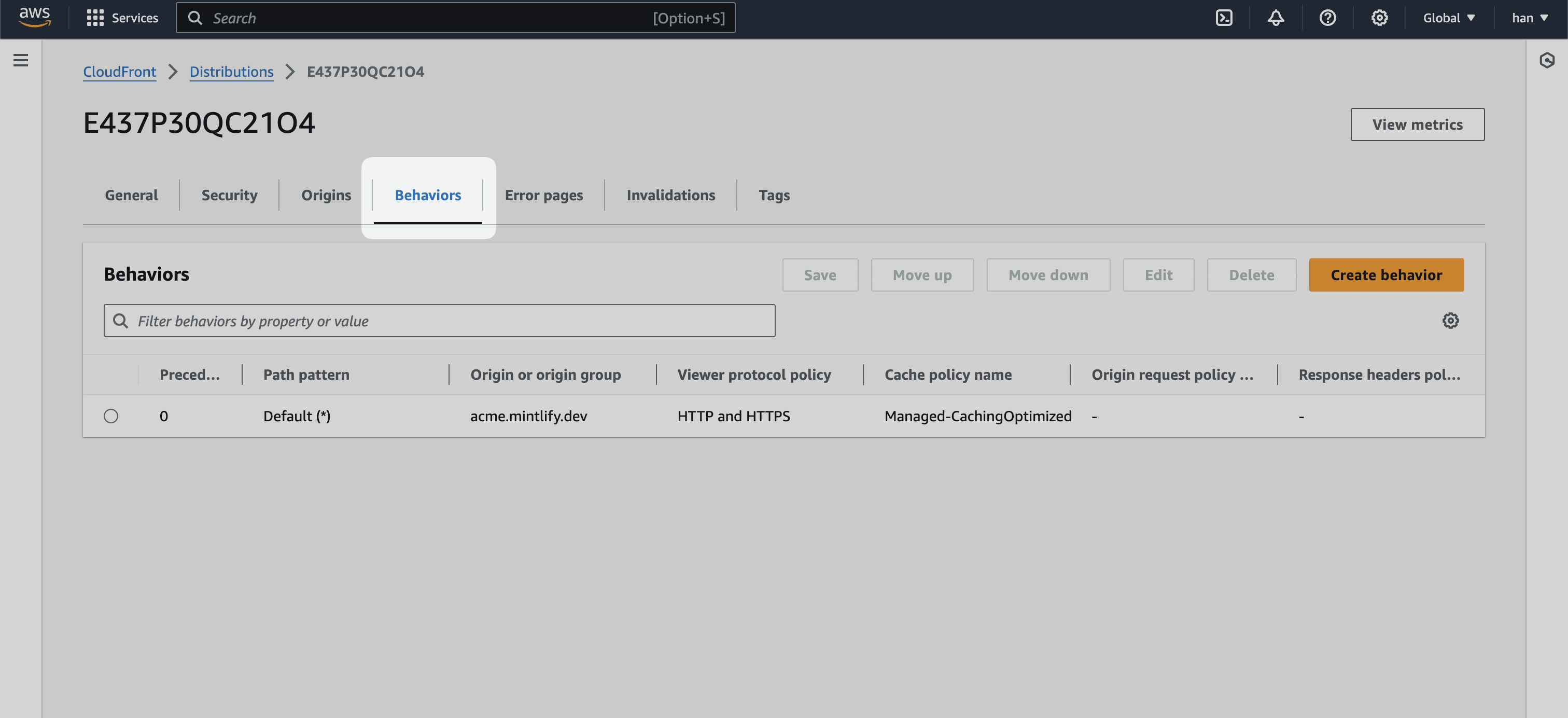
- Select the Create behavior button and create the following behaviors.
/.well-known/*
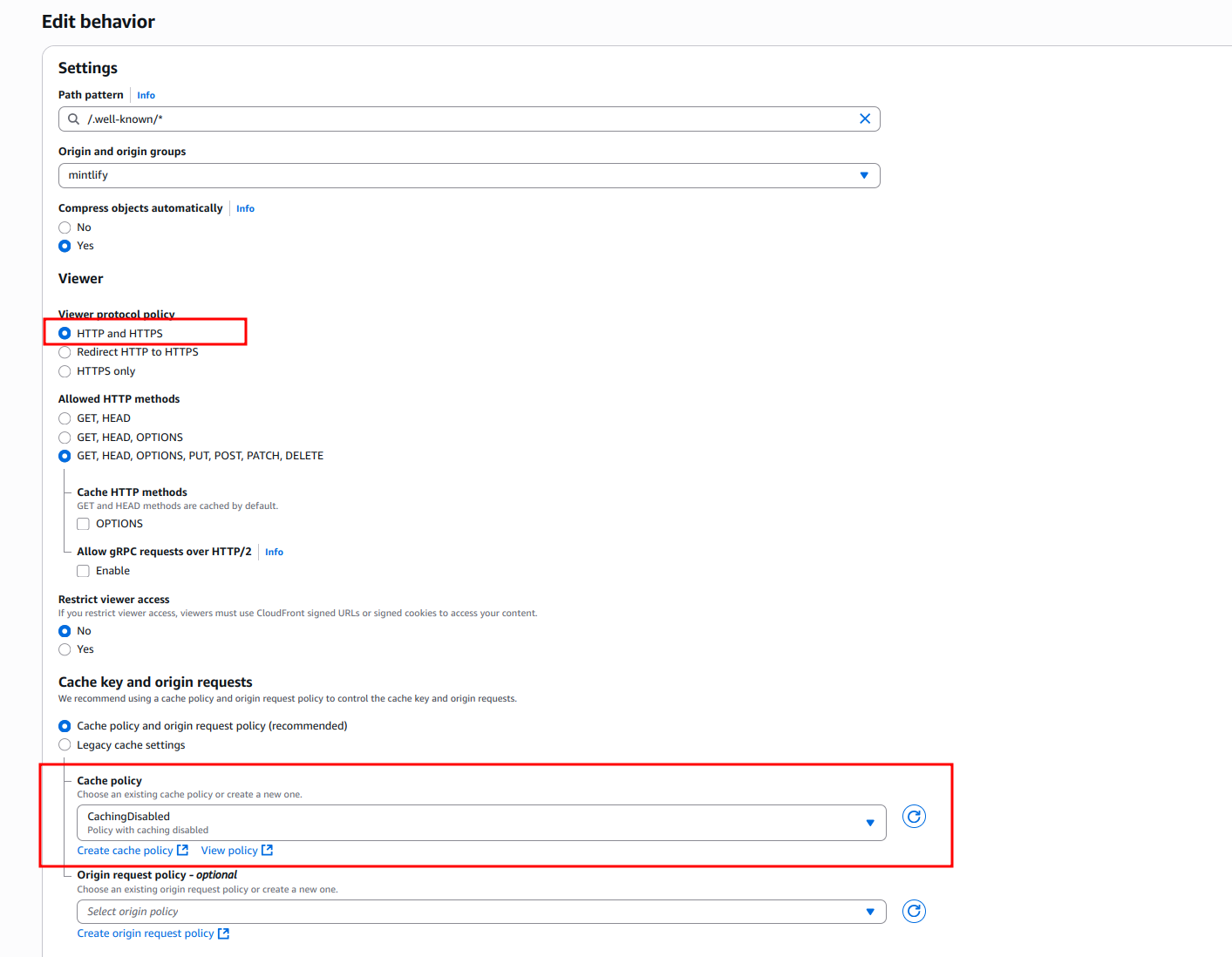
Create behaviors for Vercel domain verification paths with a Path pattern of /.well-known/* and set Origin and origin groups to your docs URL.
For “Cache policy”, select CachingDisabled to ensure these verification requests pass through without caching.
If
.well-known/* is too generic, it can be narrowed down to 2 behaviors at a minimum for Vercel:/.well-known/vercel/*- Required for Vercel domain verification/.well-known/acme-challenge/*- Required for Let’s Encrypt certificate verification
/docs
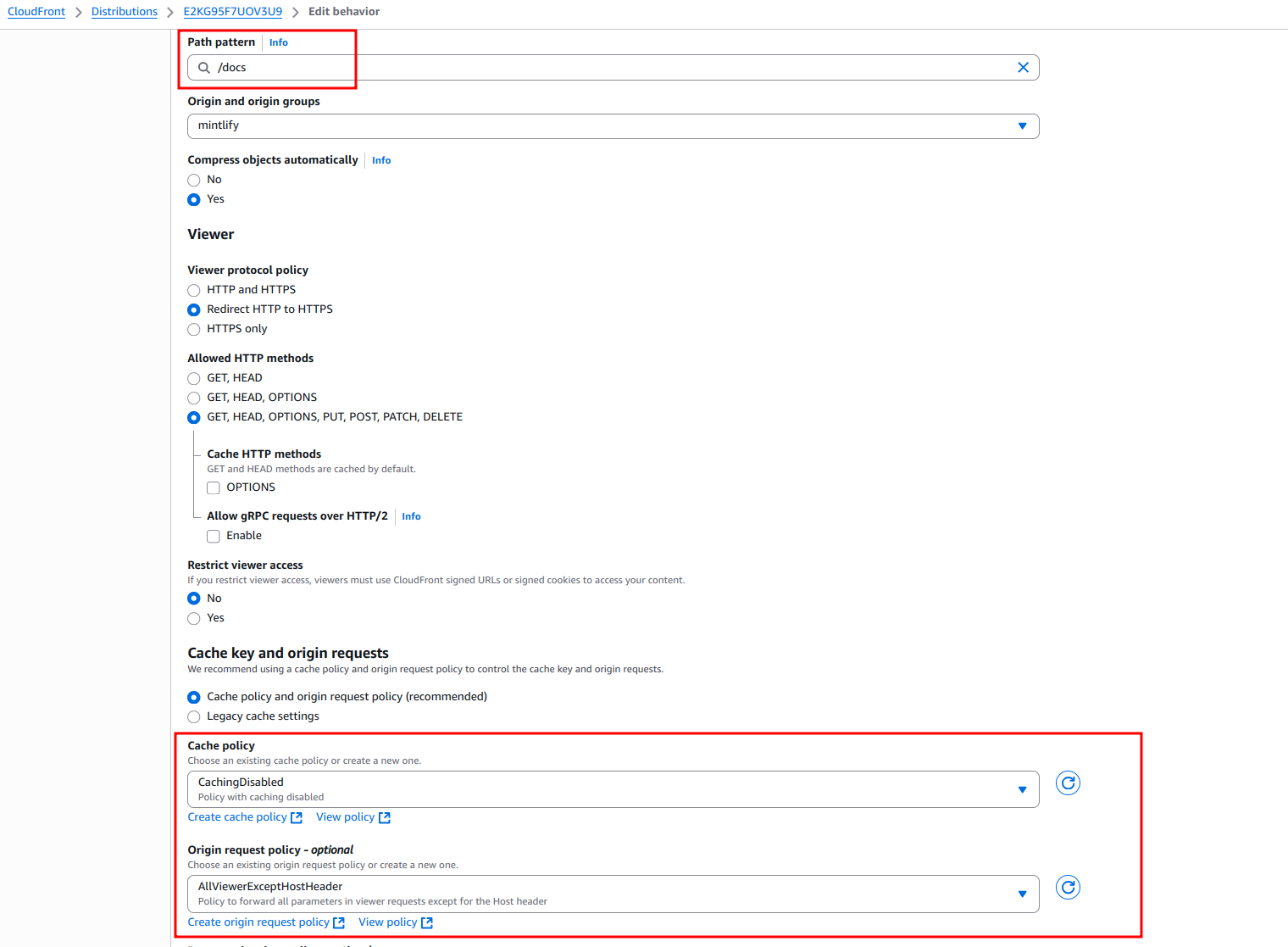
Create a behavior with a Path pattern of /docs with Origin and origin groups pointing to the .mintlify.dev URL (in our case acme.mintlify.dev).
- Set “Cache policy” to CachingOptimized.
- Set “Origin request policy” to AllViewerExceptHostHeader.
- Set Viewer Protocol Policy to Redirect HTTP to HTTPS
/docs/*
Create a behavior with a Path pattern of /docs/* and Origin and origin groups pointing to the same .mintlify.dev URL.
These settings should exactly match /docs. With the exception of the Path pattern.
- Set “Cache policy” to CachingOptimized.
- Set “Origin request policy” to AllViewerExceptHostHeader.
- Set “Viewer protocol policy” to Redirect HTTP to HTTPS
/mintlify-assets/_next/static/*
- Set “Cache policy” to CachingOptimized
- Set “Origin request policy” to AllViewerExceptHostHeader
- Set “Viewer protocol policy” to Redirect HTTP to HTTPS
Default (*)
Lastly, we’re going to edit the Default (*) behavior.
- Change the default behavior’s Origin and origin groups to the staging URL (in our case
mintlify-landing-page.vercel.app).
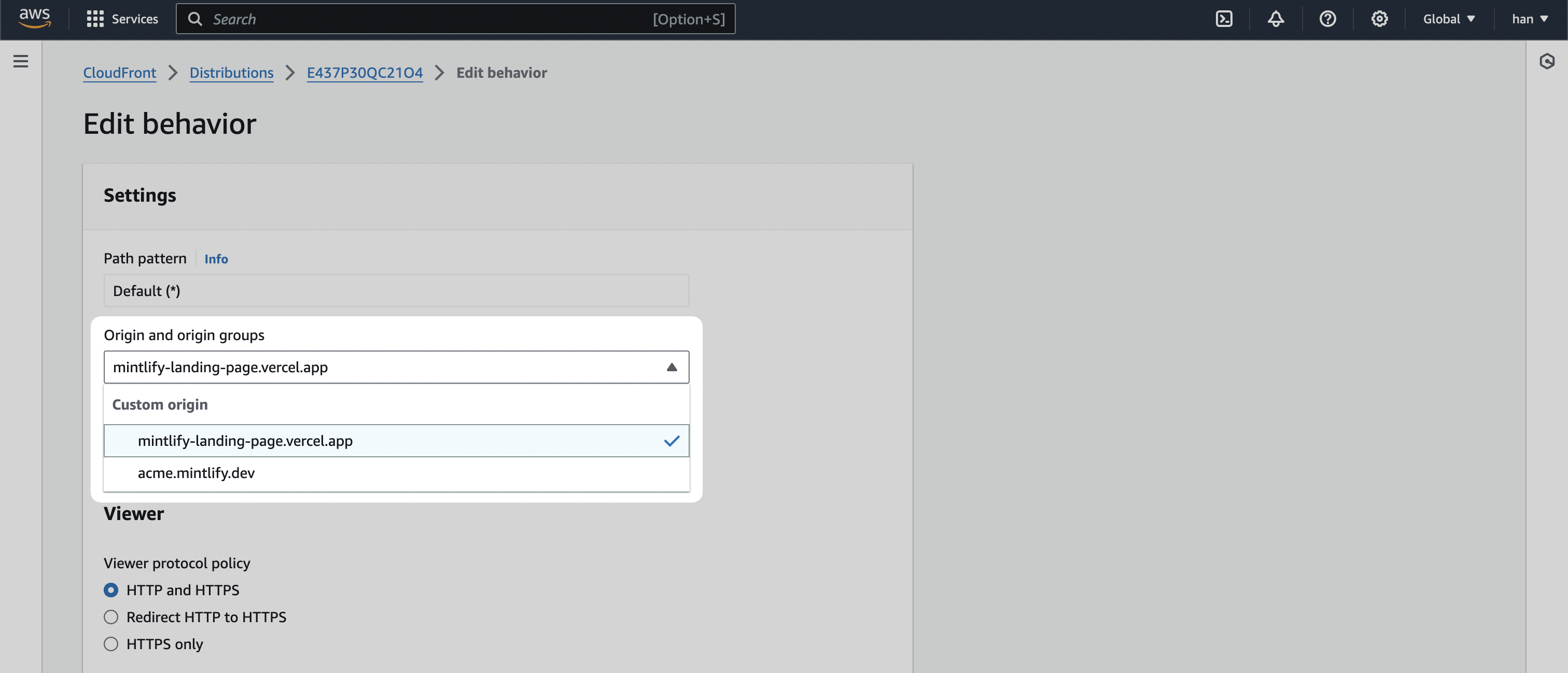
- Select Save changes.
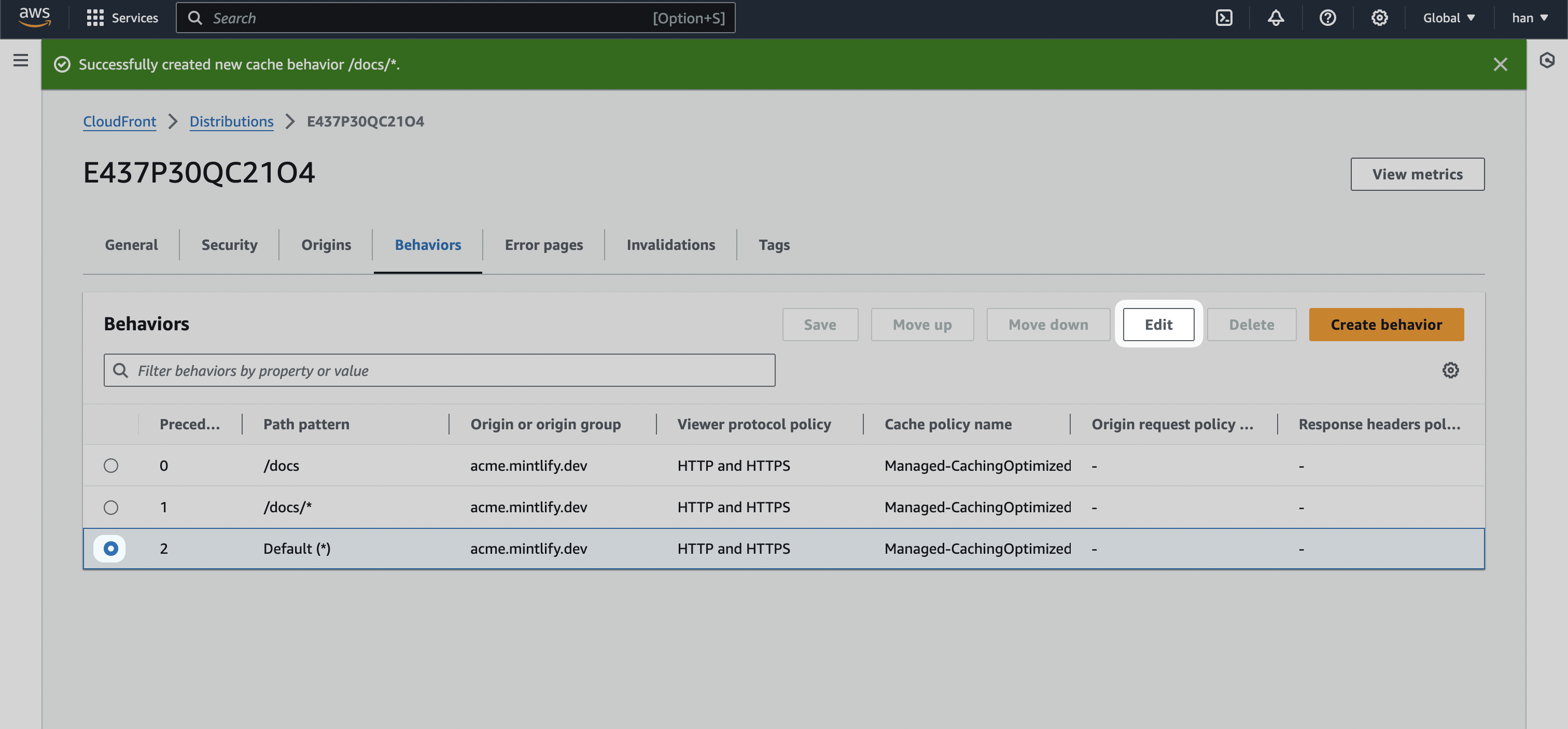
Check behaviors are set up correctly
If you follow the above steps, your behaviors should look like this:
Preview distribution
You can now test if your distribution is set up properly by going to the “General” tab and visiting the Distribution domain name URL.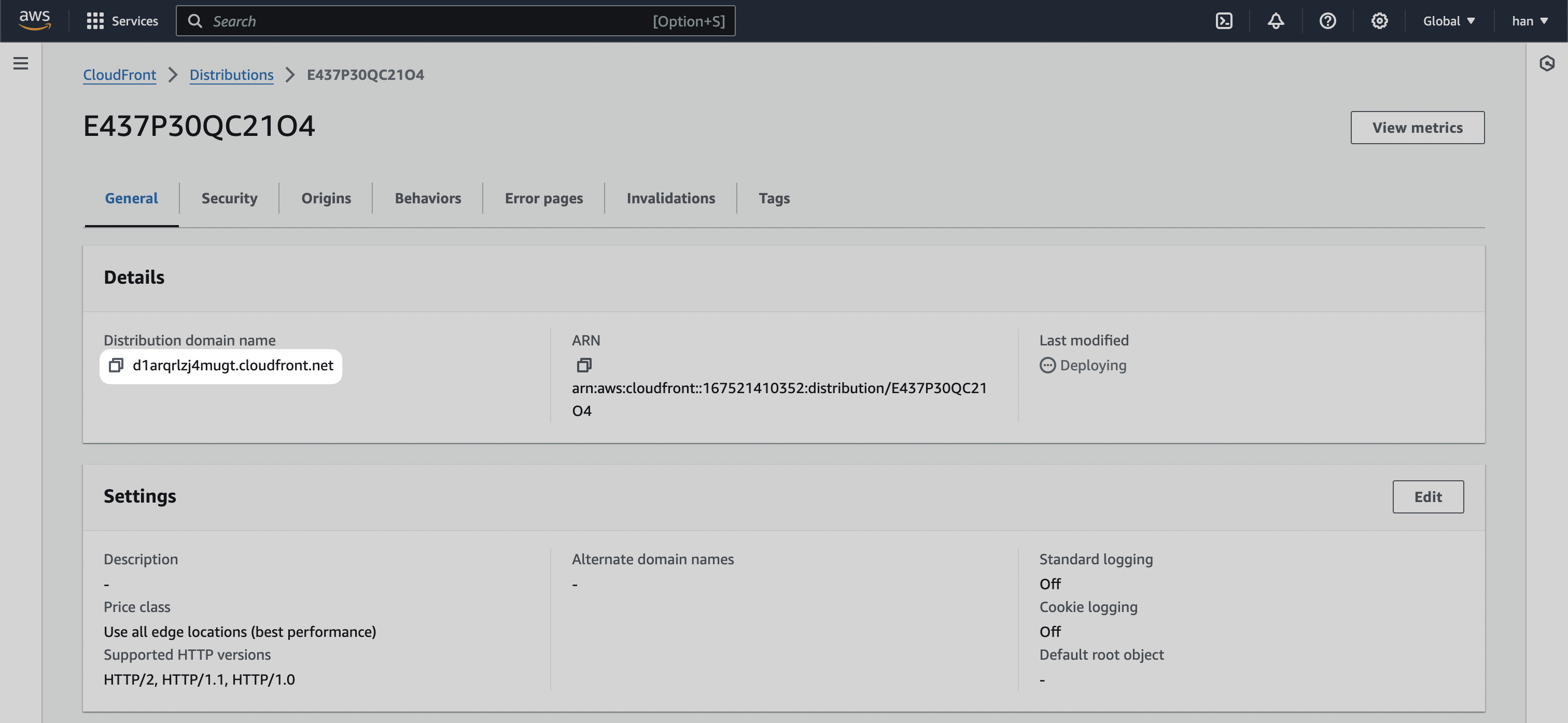
/docs to the URL, you should see it going to your Mintlify documentation instance.
Connect with Route53
Now, we’re going to bring the functionality of the CloudFront distribution into your primary domain.For this section, you can also refer to AWS’s official guide on Configuring
Amazon Route 53 to route traffic to a CloudFront
distribution
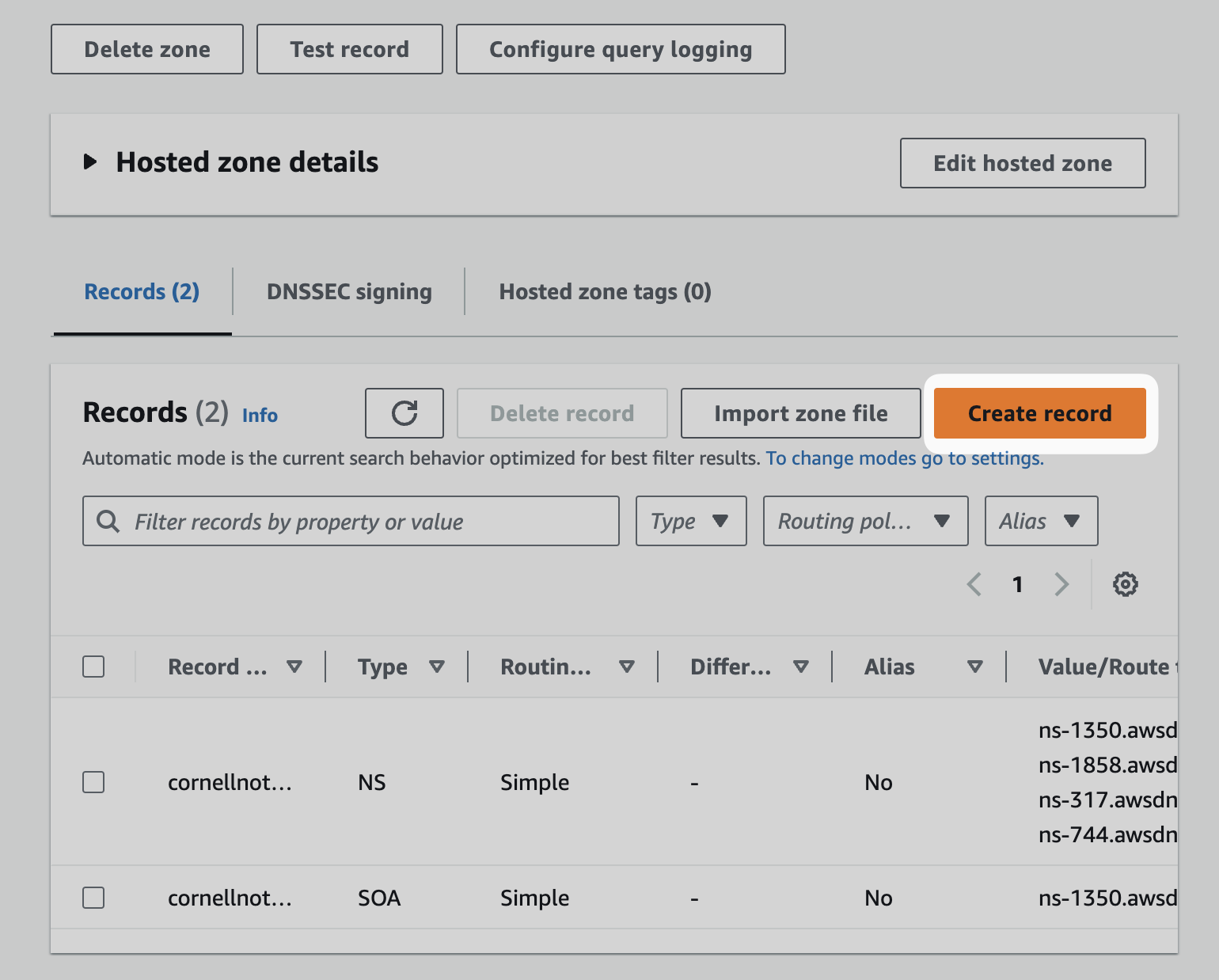
- Navigate to Route53 inside the AWS console.
- Navigate to the “Hosted zone” for your primary domain.
- Select Create record.
- Toggle
Aliasand then Route traffic to theAlias to CloudFront distributionoption.
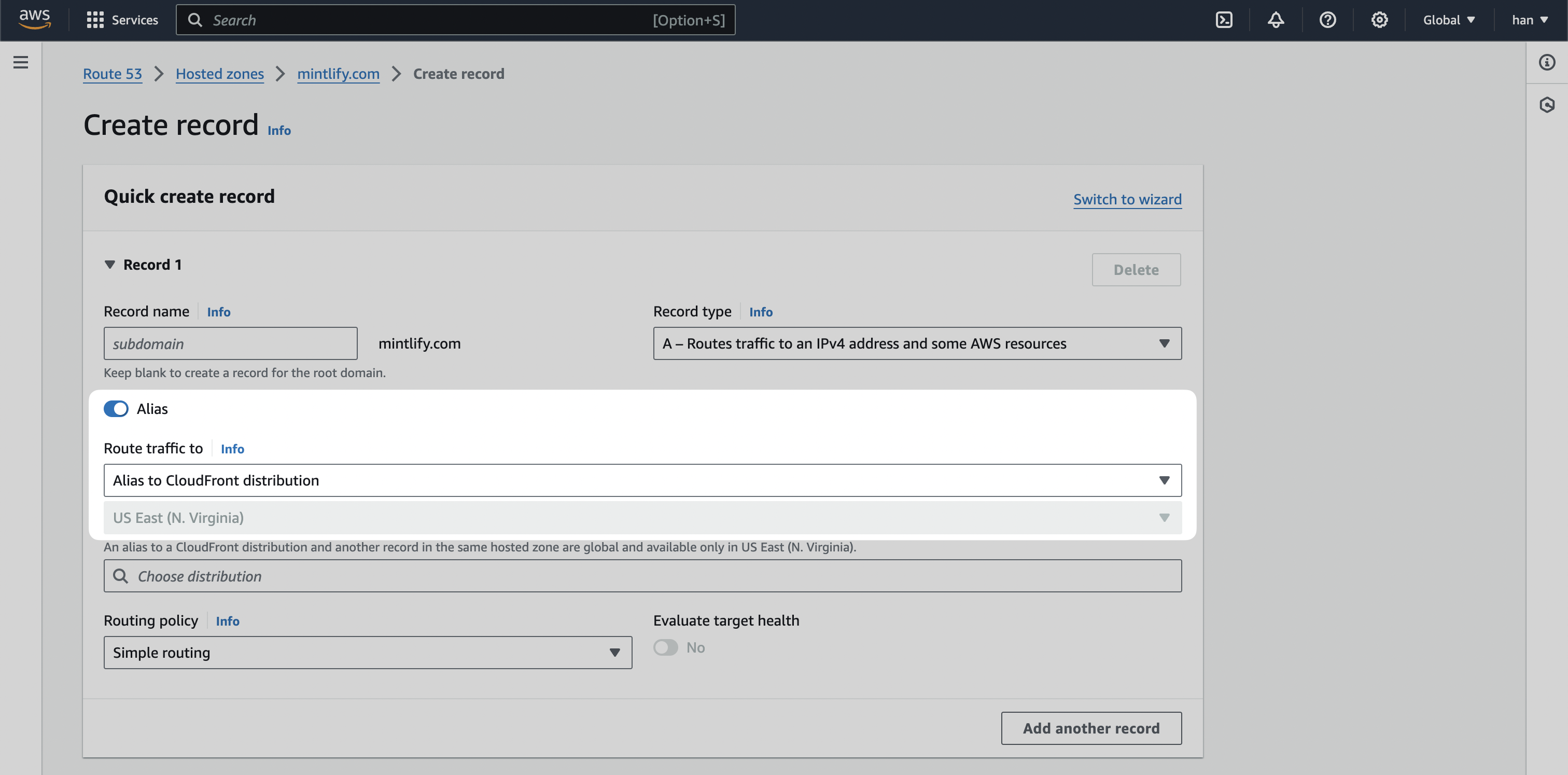
- Select Create records.
You may need to remove the existing A record if one currently exists.
/docs for your primary domain.
After configuring your DNS, custom subdomains are usually available within a few minutes. DNS propagation can sometimes take 1-4 hours, and in rare cases up to 48 hours. If your subdomain is not immediately available, please wait before troubleshooting.